Phishing for Retailer Logins
Phishing and pharming are the techniques used by cybercriminals to fool unsuspecting users into divulging their sensitive information such as a username and password on web sites that look like a legitimate site but in fact are operated by the criminals.
Phishing has been around for quite some time and the techniques have gotten increasingly sophisticated. Modern phishing attacks involve a proxy type of setup where users' actions are forwarded from the copy-cat site to the legitimate site, to where it's very hard for the user to tell that something is wrong, so such attacks often go unnoticed.
In the past, banks were the primary targets of phishing attacks. To combat this, banks have deployed anti-phishing personalization strategies and 2-factor authentication. As a result, cybercriminals are now increasingly targeting other kinds of businesses, most notably online retailers.
Phishing in the mobile world
The rapid adoption of smartphones has unfortunately greatly increased the effectiveness of phishing attacks. There are actually four factors responsible for this:
- The location bar where the url is displayed is not long enough to display the full url
- The location bar scrolls away from view when the page is scrolled
- There is no visual differentiation between HTTPS sites secured by regular SSL certificates and those with Extended Validation certificates
- There is often no location bar at all in embedded browsers inside apps
On a desktop browser, a user can look at the location bar at the top of the browser and see the full length of the domain name of the web site they are on. But on smartphones, the url is often cut off:
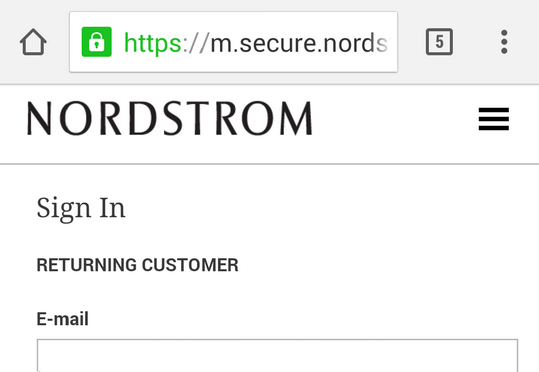
Even a savvy user will think this is the real Nordstrom site (i.e. https://m.secure.nordstrom.com) and not actually https://m.secure.nordstrom.com.hacker.com and will enter her password.
More than 10 years ago, desktop browser vendors recognized the importance of keeping the location bar visible at all times. As a result desktop browsers stopped allowing the opening of windows without a location bar. Sadly, on mobile web browsers, the location bar scrolls out of view as soon as the page scrolls. Combined with that fact that the page can be auto-scrolled programmatically upon load, this allows hackers to display a fake location bar:
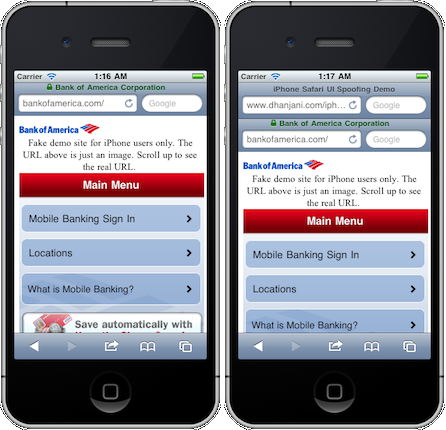
Starting with Microsoft Internet Explorer 7, desktop browsers have shown a clear differentiation between Extended Validation (EV) SSL certificates and regular SSL certificates, which can be obtained with nothing more than an email address at the domain name. Because Certificate Authorities are prohibited from issuing wildcard EV certificates, this assures that desktop browsers show the green bar (or green lock) only when the browser is on https://secure.nordstrom.com.
But on many mobile browsers, EV and regular certificates look the same, which means a wildcard certificate issued to *.hacker.com without any verification of the site owner's identity allows the fraudulent site to display the green lock on a phishing subdomain such as https://m.secure.nordstrom.hacker.com.
Finally, on mobile devices, users often view web sites not in the device's browser such as Safari or Chrome but in an embedded web viewer control inside an app. Often, developers of these apps completely leave off the location bar or any indication of the site's identity and security, so there is no way for the user to know what web site they are really on.
Phishing for online retailer passwords
There are two kinds of phishing attacks targeted at online retailer sites: the fraudulent site can ask the unsuspecting shopper to enter their payment information, so they can steal the credit card number; or the phishing site can ask the user to login, so they can capture the password.
There is really nothing the retailer can do to combat the first kind of attack but fortunately for the retailer, if the cyber thief steals the credit card number and uses it somewhere fraudulently, it doesn't create a financial liability for the phished retailer. In addition, this kind of attack is much more difficult to pull off in a way that the user wouldn't notice. Plus just convincing the user to buy something and go through the whole process to enter their payment information will be difficult. It helps that users get particularly security-conscious at the point where they have to type in their credit card number.
The capture of passwords on the other hand is both very easy and the liability for the consequences lies squarely with the retailer. Most retailers have no anti-phishing defenses and will allow hackers to login with stolen credentials, change the email address, later on place a small order to a different shipping address or for in-store pick-up (with their name specified as authorized user) without tripping any anti-fraud protections and even without notifying the owner of the credit card that their information on file has changed.
There is even a bonus for the cybercriminals with a captured password. Most users tend to use the same password (or with minor predictable variations) everywhere, so capturing that password can allow the hackers to get into other accounts that user might have online.
How can retailers protect themselves?
As with most things in security, you, the retailer, need multiple layers of defenses. First make sure that you send email notification to the email address on file if the user changes that email address in your system. Consider using a different and very distinct FROM address (including domain) and name in such emails to make sure these notices don't get overlooked or filed away automatically together with your promotional emails.
Second, require 2-factor authentication whenever the shopper initiates a sensitive change in their information on-file, such as a new email address, a different shipping address or a new user authorized to pick up an order in store. (See this blog post for more on user-friendly 2-factor authentication for online retailers.)
When an email address is changed, if you are unable to 2-factor authenticate it via either an email to the old address or an SMS message to the mobile phone number on file, or by asking the user to provide the full credit card number, you should flag the account to require manual review on the next order, regardless of how much later that order happens. During that review be sure to call the shopper and get the credit card number from them again to authenticate them.
The above measures will help but ultimately the only guaranteed way to protect yourself against password phishing (and stop torturing your customers with password hassles) is to do away with user passwords completely with a password-less login solution like CardPass.